SLA Company Limited is distributor of EgoSecure, distribute and support EgoSecure Endpoint product to resellers, endusers in Vietnam. Access control, Antivirus, Application control, Mobile device management, Folder encryption, Full disk encryption, mail encryption.
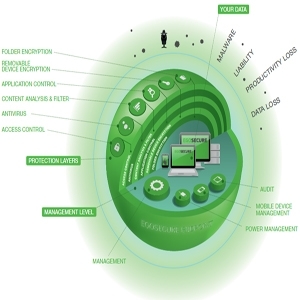
EgoSecure endpoint protection help to manage and protect your endpoints in IT system safely, be easy to control and have actions.
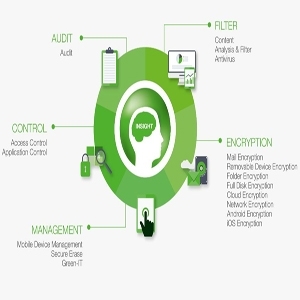
Core functionality
– All EgoSecure Endpoint components are managed through the single Administrators’ console. There is no need to switch between different management consoles and configuration options of different applications. There is only one agent installed on protected endpoints. This agent contains all CAFE components (responsible for Control, Audit, Filter and Encryption) so there is no need to deploy separate agents for different tasks. The system is light and clear.
– Control functionality allows managing which groups of users are allowed to use what types of devices depending on the business requirements. For some groups of users it is possible to block all removable media and network devices completely, other settings allow to provide read-only access to media, temporary or scheduled access based on time restrictions etc. Administrators can use pre-defined classes of devices and types, in addition to this they can configure more granular access rights based on models or individual devices.
– Audit functionality allows recording all user file activities with removable media. It is possible to track what files the user introduced on removable media, what data was written on it etc. In order to comply with privacy regulations and works council requirements it is possible to set up the product in such a way that administrator alone cannot access this data. The product supports scenario where access to audit records is only possible together with a representative of the workers’ council or the management, for this case access is restricted by to two passwords.
– Filter is working in both directions allowing not only to check what types of files can be written to external media but also to check what data the users can bring on these devices. One simple rule can completely block all executable files on any removable media eliminating malware.
– Encryption component performs per-file transparent background encryption of data written to removable media. This insures that even if USB stick is lost or stolen the information will not fall into the wrong hands. Compared to container-based encryption there is no need for initial setup of every container and every device. Only authorized users will be able to access encrypted data. The process of encryption and decryption is absolutely transparent for the user so there is no need additional education.
EgoSecure Endpoint Management
– System requirements are very simple in terms of hardware configuration. There are no complicated dependencies from additional software components like Microsoft .Net Framework, Java, IIS, Apache etc. which means faster deployments. There is no need to install additional components before the product installation and maintain them afterwards e.g. apply service packs and patches to close discovered vulnerabilities. The only required additional component is SQL database. MySQL and Microsoft SQL are supported as well as free edition of Microsoft SQL Express.
– The product supports Microsoft Active Directory, Novell eDirectory and OpenLDAP directory services. As a result administrator can effectively use existing logical structures and hierarchies of organizations like User Groups, Organization Units and Computers rather than building the new structures from scratch. This saves time and configurations efforts and allows matching business structures with security policies the most efficient way.
– Changing the Active Directory schema usually requires careful planning; as a result Domain Administrators are often against such changes. There might be problems if domain controllers and endpoints are managed by different administrators. In case of EgoSecure there are no changes made to the Active Directory scheme, the product is working with the synced copy of current Directory Services. Standard active directory “read” access rights (e.g. Domain User) are enough.
– The product allows creation of custom MSI installation packages. Such pre-configured installers can include the address of the management server as well as pre-configured access rights and policies “built in” inside. Such custom MSI packages can be deployed via GPO or other 3rd party management tools. It is also possible to deploy such packages to enforce policies on standalone computers without any network connectivity or when any connection to EgoSecure management server is not possible.
– Reboot is not required for Endpoint Management Server installation. This means there is no need to schedule specific time for deployment, user business-related activities are not interrupted.
– All policies are enforced and all changes are applied immediately. Unlike solutions where endpoint policies are managed through Domain Group Policies there is no need to wait until the next policy refresh (which is 90 minutes by default) or ask the user for manual policy refreshment via command line instructions which are really hard to explain to the users without IT background. There are no such cases when the user has to log off and then log in back in order to bring into effect changes made by administrator.
– In the majority of cases the user has information access rights, not computer. This means that the user is the primary element of policy enforcement. It is important to take this into consideration in both cases: when the user can possibly use different computers or when there are different users working on the same computer. The only right model is when the policy follows the user no matter where he is logged in from. Computer-based restrictions can take an effect for Internet-kiosk and some other rare cases. Only in this case they override user-based rights. EgoSecure Endpoint support all such scenarios, it is built according to the structures and needs of real organizations.
– Many competitive solutions are built with computer-based policies in mind e.g. Endpoint solutions which are based on or derived from standard anti-virus solutions. Anti-Virus policy was always applied to protected endpoints while information protection and access rights are obviously not computer-based; they are user-based by nature with rear exceptions mentioned above.
– After restrictions were applied it is fairly simple to make important exceptions later on to allow users to carry out their important job-related activities. Users can simply request additional access rights through EgoSecure Endpoint Agent interface and administrators can view such requests and assign appropriate rights with a mouse click. This simplifies communication between the users and security administrators or helpdesk employees; the users will receive the rights exactly which they are asking for.
– Sometimes it is important to apply exceptions and change access permissions when the user is working on the road and restrictions are blocking useful activities. EgoSecure solves this problem through powerful challenge-response system of activation codes. This allows changing the rights without having any network access to the target system e.g. when such system is completely offline.
– Product interface is so clear and simple that administrators can deploy and configure protection across the enterprise in a matter of minutes without minimal references to product documentation.
EgoSecure Endpoint Components
– Access control: Access control protects companies against “internal attackers” by controlling which persons within the company need access to which data.
– Audit: Audit ensures the transparency of all protection measures and allows you to capture forensic data. This optional auditability of EgoSecure Endpoint is an important contribution to ensure IT compliance. As a matter of course, compliance with your employees personality rights and labor laws is also ensured (4-6-eye principle).
– Antivirus: An antivirus solution provides proven protection against anonymous attackers from the Internet. It is important to ensure a high detection rate to be able to respond very quickly to new viruses and Trojans. EgoSecure Endpoint integrates a leading-edge solution with an acknowledged high detection rate.
– Application control: Application Control controls which user is allowed to start which programs, for instance, to prevent that games or unlicensed software products are used to avoid liability risks and economic damage. It is also possible to block most viruses, even before antivirus solutions have detected them.
– Power management: Intelligent power management ensures efficient device operations by ensuring that energy is only consumed when the computer is actually used. Power Management helps reduce IT operational costs while also contributing to the company’s environmental balance and ensuring a fast ROI for the EgoSecure Endpoint implementation.
– Secure erase: Secure erase ensures that deleted files cannot be recovered, no matter whether the file is located on your internal hard drive or on an external storage medium. The software offers multiple ways of deletion. Users have the option to immediately delete documents – including their mirror copies – or to destroy all the deleted files regularly on a schedulable base. In case of sale or final phasing-out of hardware SecureErase ensures that you are only giving away your hardware.
– Mobile device management: The increasing degree of adoption of mobile devices such as tablets or smartphone must also be reflected in corporate security architectures. Mobile Device Management ensures the intelligent integration of mobile devices, including support of the Android and iOS operating systems.
– Removable device encryption: Mobile media such as USB sticks are important means to support increasingly flexible business and working environments. While devices are shrinking in size and increasing in performance, they are also lost or stolen more easily. Removable Device Encryption ensures that the data cannot be used by unauthorized parties. Password-based encryption and decryption can be achieved on any Windows computer, with full transparency for authorized users. Encryption is file-based, and various encryption types are available (for the whole company, for individual users or for certain user groups). It is possible to use multiple encryption types for one medium.
– Folder encryption: Folder Encryption protects data on lost notebooks or hard drives and also secures individually defined sensitive data on systems that can be accessed by multiple users. For instance, highly sensitive management data can be protected against access through employees with many privileges, such as IT staff.
– Full disk encryption: Full Disk Encryption provides comprehensive protection of all devices and encrypts the complete hard disk or partitions on the sector level. The solution also provides on-demand pre-boot authentication to authenticate users before the operating system is started. Automatic detection of new hard disks in the integrated encryption chip, lightning- fast initial encryption and the centralized management ensure the seamless integration with existing IT infrastructures.
– Bitlocker management: A central management of BitLocker is impossible with Microsoft Onboard resources. BitLocker management offers automatic management of BitLocker-enabled drives in the Central EgoSecure management console. With one click, the encryption and decryption, as well as the blocking of a storage device can be processed. Devices are automatically checked for their BitLocker compatibility. The key management, as well as the archiving of the recovery keys can be performed centrally.
– Mail encryption (virtual appliance – VMware ESX and Microsoft Hyper-V): Mail Encryption ensures the safe exchange of e-mails; no software needs to be installed for this purpose on the receiving or transmitting system. Encrypted e-mails with an electronic signature can be sent and read within the user’s familiar environment. It is also easy to encrypt and transport very large e-mails.
– EgoSecure mail encryption user license: Mail Encryption ensures the safe exchange of e-mails; no software needs to be installed for this purpose on the receiving or transmitting system. Encrypted e-mails with an electronic signature can be sent and read within the user’s familiar environment. It is also easy to encrypt and transport very large e-mails.
For more information about EgoSecure endpoint protection, please contact with SLA Company Limited here or Vietnamese site.